Protect Everything with Microsoft Security
Comprehensive, cost-effective security with a single platform
Protecting your entire digital estate by leveraging the power of:
Microsoft Sentinel for visibility across your entire organization
Microsoft 365 Defender to help secure your end users
Microsoft Defender for Cloud to help secure your infrastructure

Security Workshop
The NIST Cybersecurity Framework
In this workshop we will leverage the NIST Framework, going over each of its 5 areas together: Identify, Protect, Detect, Respond, and Recover
The National Institute of Standards and Technology (NIST) has developed a set of guidelines for organizations looking to manage and mitigate cybersecurity-related risks. The framework is organized into five core cybersecurity “functions”:
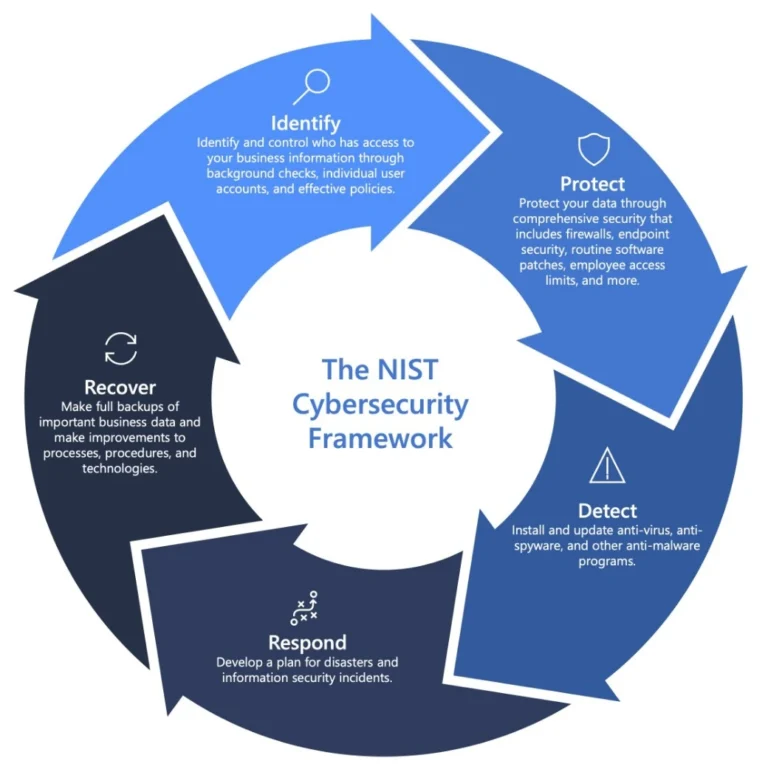
Identify
01 : Key security findings
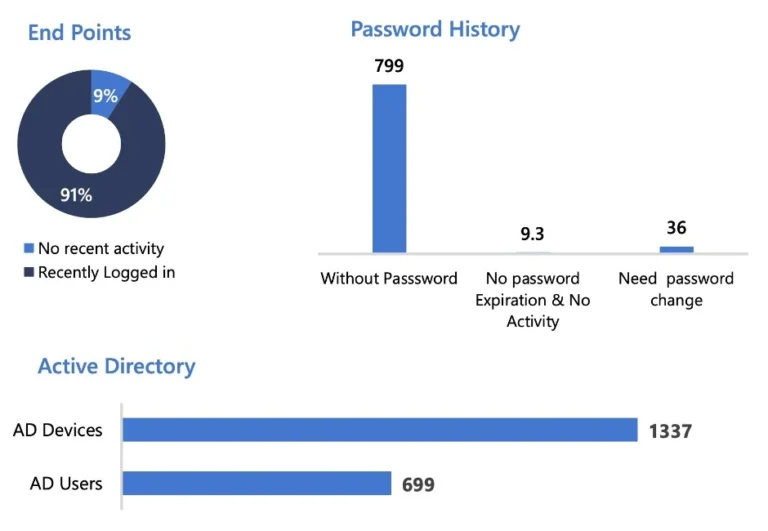
- We found 64 of 636 accounts with no recent activity during the assessment.
- 799 accounts show potential password vulnerabilities, 36 need password change.
Inactive user accounts are a significant security issue, as former employees and external attackers could use those accounts to harm the organization. Inactive accounts also use up space in the directory database that could be reclaimed.
Discussion tools :
Y
N
M
02 : Important security questions
Would you like to protect company email and files on both person all owned and company-provided devices?
Yes
No
I don’t know
Would you like the ability to distinguish different levels of access for users depending on factors such as their organizational role, location, or device compliance?
Yes
No
I don’t know
03 : Potential actions to discuss (mark all that apply)
Leverage Azure Active Directory with:
- Conditional Access Policies
- Multi-factor Authentication
- Role-based Access Control (RBAC)
Leverage external identities with Azure AD to securely manage external users in your IT environment.
Use time-based role assignments with Azure Privileged Identity Management.
Use Azure Key Vault to manage access to application keys and secrets for secure authentication.
Protect
01 : Key security findings
- We noticed 191 endpoints lack standardized endpoint protection
- While 21 machines are not patched/protected for common ransomware threats
Discussion tools :
Y
N
M
02 : Important security questions
Does your organization have specific legal or regulatory requirements (e.g., GDPR, HIPAA, PCI, ISO) to comply with or work with high sensitivity data?
Yes
No
I don’t know
Would you like to ensure all users are protected from software threats with centralized configuration and enforcement policies?
Yes
No
I don’t know
Would you like to protect sensitive emails and documents with encrypted access so that they can only be viewed, edited or shared by specified users?
Yes
No
I don’t know
03 : Potential actions to discuss (mark all that apply)
Implement Azure Security Center to manage and secure resources.
Leverage Microsoft Sentinel to provide automated protection for malicious activity.
Implement Azure Information Protection to setup data loss prevention policies.
Setup Azure Policies to set standards on users interacting with IT resources.
Protect accidental loss or updates to data with Azure Resource Manager.
Action plan
Let’s use this section to capture our main takeaways from the workshop
Identify
| IDENTIFY ACTIONS | FEATURE | CRITICALITY |
|---|---|---|
| Implement Multi Factor Authentication for users | AAD | High |
| Setup conditional access policies for trusted locations | AAD | Medium |
Protect
| PROTECT ACTIONS | FEATURE | CRITICALITY |
|---|---|---|
| Implement Mobile Application Management (MAM) using a combination of App Protection Policies and Conditional Access to require approved apps on mobile devices. | AAD | High |
| Use Office 365 Message Encryption (OME) or Sensitivity Labels to classify and protect higher sensitivity email messages. Communication channels in Microsoft 365 are encrypted by default. | AAD | Medium |
| Collaboration governance (e.g. Groups and sharing settings), Data Loss Prevention policies. Periodically review access. | AAD | Low |
| Use Security Defaults or a Conditional Access policy to require Multi-factor authentication for all user accounts. Also consider SSO for other Enterprise Applications, or requiring MFA wherever possible. | AAD | High |
| Regularly perform audit of active accounts (users and devices); this goes for all systems, not just those in Azure AD and Microsoft 365. | AAD | Low |
| As regards Microsoft 365, there is currently no automated process for this, however you can use a script to seek out and prune stale accounts. | AAD | Low |
Trust your business with the Pros, and eliminate the technology challenges holding you back from greater success.




